The electronic signature in French law

The recognition of electronic signature in France is established byArticle 1367 of the Civil Code which states:
Article 1367
Amended by Ordinance No.2016-131 of February 10, 2016 – Art. 4
The necessary signature to the perfection of a legal act identifies its author. It expresses its consent to the obligations arising from this act. When it is affixed by a public officer, it confers authenticity on the act.
When it is electronic, it consists of the use of a reliable identification process to ensure its connection with the act to which it attaches itself. The reliability of this process is presumed, until proven otherwise, when the electronic signature is created, the identity of the insured signatory and the integrity of the guaranteed act, under conditions set by decree in the Council of State.
The civil code therefore gives us the minimum so that a digital process can be recognized as an electronic signature: the use of a reliable identification process guaranteeing its link with the act to which it attachesitself.
The reliability of this process is therefore presumed until proven otherwise when the conditions set by the Council of State are met, here they are:
Article 1 of Decree No. 2017-1416 of September 28, 2017 relating to electronic signature
The reliability of an electronic signature process is presumed, until proven otherwise, when it implements a qualified electronic signature.
A qualified electronic signature is an advanced electronic signature, in accordance with Article 26 of the aforementioned regulation and created using a qualified electronic signature creation device that meets the requirements of Article 29 of that regulation, based on a qualified electronic signature certificate that meets the requirements of section 28 of this regulation.
Let us sum up what is said in French law:
An electronic signature is the use of a reliable identification process to ensure its connection to the act to which it attaches itself. A qualified electronic signature as defined by eIDAS is deemed reliable until proven otherwise.
Qualified signature therefore has an advantage related to its main disadvantage: it reverses the burden of proof, it is up to the person challenging the act of proving that consent, or the act, is not in compliance. But the flip side of this indisputability is the cumbersome procedure for issuing, handing over and using the qualified certificate, which disqualifies qualified electronic signature in many exchanges where speed and flexibility are sought.
But what interests us here is the unqualified digital signature which can now be used in French law in all cases where qualified electronic signature is not required. That is, in the vast majority of cases.
The eIDAS regulation: definition of electronic signature at European level
Now that we have seen the difference between the two types of signatures in French law, the question arises of their use with third parties located in the European Union.
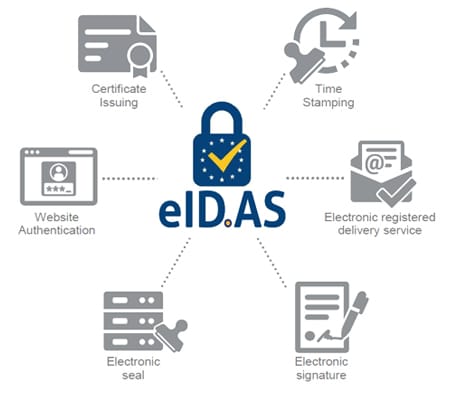
The eIDAS regulation distinguishes four types of electronic signatures:
The simple electronic signature (defined in Article 3, point 10 of the eIDAS regulation):
This signature includes data in electronic form, which is logically attached or associated with other data in electronic form and which the signatory uses to sign.
Advanced electronic signature (defined in Article 26 of the eIDAS Regulation):
This signature must:
– Be bound to the signatory in a unequivocal manner;
– To identify the signatory:
– Have been created using electronic signature creation data that the signatory can use under its exclusive control with a high level of trust;
– Be linked to the data associated with it so that any subsequent changes in the data are detectable.
Advanced electronic signature based on a qualified certificate (defined in Articles 26 and 28 of the eIDAS Regulation):
This signature must be based on a qualified electronic signature certificate that complies with the requirements contained in Appendix I of the eIDAS Regulation. The processes for verifying the identity of the applicant, issuing and managing the lifecycle of a qualified electronic signature certificate meet important security requirements, which ensure that the certificate is not properly issued only to the legitimate signatory.
Qualified electronic signature (defined in Article 3, item 12 of the eIDAS regulation):
Qualified electronic signature must be based on a qualified electronic signature certificate, implemented through a Qualified Electronic Signature (QSCD) creation device. Such a scheme guarantees, with a high level of confidence, that the signature can only be carried out by the legitimate signatory. This device is the subject of a certification decision by a national authority.
The eIDAS regulation defines confidence levels in electronic signatures more finely than in French law, but it leaves to the assessment of each member state the level required according to the documents to be signed, except for the rare cases where the Qualified electronic signature is required.
The eIDAS regulation will therefore serve as a reference to qualify an electronic signature and the most serious signature platforms such as Docage Signature offers a signature that corresponds to the criteria of advanced electronic signature.
Example of advanced electronic signature with Docage Signature

| Advanced Signature Criterion | Signature Docage |
|---|---|
| Be bound to the signatory in a unequivocal manner | Issued by a European trusted provider a certificate on behalf of the signatory |
| Identifying the signatory | Using dual-factor email/sms identification |
| Have been created using electronic signature creation data that the signatory can use under its exclusive control with a high level of trust | The certificate is issued only when the signatory enters the SMS code that he can only view on his phone for which he has exclusive use |
| Be linked to the data associated with it so that any subsequent changes in the data are detectable | The unalterability of the document, consent and link between them is guaranteed by a certificate issued by a European trusted provider |
| Method of identification | safety | easiness | Cost |
|---|---|---|---|
| Invitation to sign by email without code | 1/5 | 5/5 | 1/5 |
| Invitation to sign by email – Single-use code received by email | 2/5 | 5/5 | 1/5 |
| Invitation to sign by email – Single-use code received by SMS | 3/5 | 4/5 | 2/5 |
| Handwritten signature on a touch screen | 0/5 | 2/5 | 1/5 |
| Scanning an ID | 3/5 | 3/5 | 1/5 |
| Scanning ID – ID Verification System | 4/5 | 3/5 | 3/5 |
| Voice print | 2/5 | 3/5 | 1/5 |
| Using a qualified certificate | 5/5 | 2/5 | 5/5 |
Comparatif des modes d’identification pour la signature électronique
Si le règlement eIDAS définit les conditions de la signature électronique avancée, le mode d’identification du signataire est appréciable par chaque prestataire et chaque utilisateur, chacun peut ainsi choisir sa méthode et peut la renforcer à sa guise dans les limites techniques offertes par la plateforme de signature.
Voici les modes d’identification possibles pour une signature électronique en l’état de la technique :
| Méthode d’identification | Sécurité | Facilité | Coût |
|---|---|---|---|
| Invitation à signer par email sans code | 1/5 | 5/5 | 1/5 |
| Invitation à signer par email + Code à usage unique reçu par mail | 2/5 | 5/5 | 1/5 |
| Invitation à signer par email + Code à usage unique reçu par SMS | 3/5 | 4/5 | 2/5 |
| Signature manuscrite sur un écran tactile | 0/5 | 2/5 | 1/5 |
| Numérisation d’une pièce d’identité | 3/5 | 3/5 | 1/5 |
| Numérisation d’une pièce d’identité + Système de vérification de pièce d’identité | 4/5 | 3/5 | 3/5 |
| Empreinte vocale | 2/5 | 3/5 | 1/5 |
| Utilisation d’un certificat qualifié | 5/5 | 2/5 | 5/5 |
Pour mieux vous guider voici les avantages et les inconvénients de chaque méthode d’identification utilisable par la signature électronique :
Invitation à signer par email sans code :
-
- Avantages :
– On peut signer avec un seul dispositif sur lequel on a accès à sa boîte mail. - Inconvénients :
– On peut signer par inadvertance car un simple clic sur un bouton suffit.
– Système mono identification
- Avantages :
Invitation à signer par email + code à usage unique reçu par email :
-
- Avantages :
– On peut signer avec un seul dispositif sur lequel on a accès à sa boîte mail. - Inconvénients :
– On peut signer par inadvertance car un simple clic sur un bouton suffit.
– Système mono identification
- Avantages :
Invitation à signer par email + code à usage unique reçu par SMS :
-
- Avantages :
– On peut signer en déplacement.
– Système double authentification - Inconvénients :
– Un tiers ayant accès au téléphone du signataire peut signer à sa place
– Le signataire doit utiliser un téléphone dont la ligne est à son nom ou au nom de son entreprise
- Avantages :
Signature manuscrite sur un écran tactile :
-
- Avantages :
– Action similaire à une signature manuscrite - Inconvénients :
– La signature générée est numérique et de mauvaise qualité, elle peut donc facilement être reproduite et contestée par le signataire.
- Avantages :
Numérisation d’une pièce d’identité :
-
- Avantages :
– Action simple à réaliser avec un smartphone - Inconvénients :
– Nécessité d’avoir une pièce d’identité au moment de la signature.
– L’accès à la pièce d’identité du signataire ou à une copie numérisée antérieurement permet de signer à sa place.
- Avantages :
Numérisation d’une pièce d’identité + Système de vérification de la pièce d’identité :
-
- Avantages :
– Action simple à réaliser avec un smartphone - Inconvénients :
– Demande plus de temps car le système passe par un tiers vérificateur
– La correspondance entre la photo sur la pièce d’identité et la photo du signataire n’est pas toujours reconnu notamment lorsque la pièce d’identité date de plusieurs années
- Avantages :
Utilisation d’un certificat qualifié :
-
- Avantages :
– Seule vérification d’identité présumée fiable par la loi - Inconvénients :
– Nécessite un dispositif qualifié remis par un prestataire de confiance qualifié
– Nécessite l’utilisation d’un ordinateur pour utiliser le dispositif
– Rares sont les signataires qui en dispose, même chez les professionnels
- Avantages :
Comme vous pouvez le voir, toute méthode a ses avantages et ses inconvénients, les méthodes sont cependant cumulables pour éliminer certains inconvénients et gagner en fiabilité.
Il faut noter que tous les systèmes cités ont une valeur juridique (plus ou moins forte vous l’aurez compris) dès lors qu’ils sont adossés à des certificats émis par un prestataire de confiance comme et à un dossier de preuve retraçant le parcours de la transaction comme le fait Docage Signature.
Il appartient à l’utilisateur de choisir la méthode la plus appropriée à son cas d’usage.
Pour en savoir plus sur l’état de l’art en matière d’identification à distance, vous pouvez consulter cet article complet publié par la Banque de France.









